Table of Contents
- What is AWS, really?
- Why think about AWS tunneling?
- What are some ways to do AWS tunneling?
- What should you keep in mind when using AWS tunneling?
When you think about working with online services, especially those that hold a lot of important information, getting to them safely is a very big deal. Amazon Web Services, or AWS as many call it, is a really big name in this area. It's a place where businesses and people can put their computer programs and information, and it offers a vast array of tools and ways to get things done. You might be curious, then, about how you can make sure your connection to all this goodness stays private and protected, so, too it's almost like building a secret passage just for your data.
- Iot Vnc Over Internet Free
- Has Barron Trump Been On Americas Got Talent
- Miaz Girthmaster Full Video
- How To Ssh Into Raspberry Pi Outside Network
- Best Remoteiot Behind Router For Raspberry Pi
This idea of creating a secure passage, often called "tunneling," helps you reach your cloud resources without worrying about prying eyes. It’s a way to make sure that when you send or get information from your AWS setup, it travels through a protected path. Think of it as putting your sensitive messages inside a strong, sealed tube that goes directly from your computer to the services you need, bypassing any open, less safe routes that might be around. This sort of direct, protected link is, in some respects, a core part of keeping your cloud operations sound.
Getting your arms around how to set up these kinds of connections is a useful skill for anyone working with online systems, particularly those built on a platform as widely used as AWS. It helps you keep your information safe and sound, whether you are just starting out or managing a large collection of services. Knowing how to do this means you can access your stuff from almost anywhere with a good bit of confidence, which is pretty important these days, you know, when so much of our work happens online.
What is AWS, really?
Amazon Web Services is, actually, a very big set of tools and services for computing that lives on the internet. It’s like having a giant data center at your fingertips, but without the need to buy or look after any of the physical computer parts yourself. People often say it's the most complete and widely used cloud system out there, and that's because it gives you so many different ways to do things, from simple storage to really advanced computer thinking. It’s a place where new companies, big businesses, and even important government groups put their trust for their online needs, basically.
- Is Megan Moroney A Trump Supporter
- Laraarose
- Was Barron Trump On Americas Got Talent Real
- Is Ron Goldmans Father Still Alive
- Joanna Gaines Illness
How does AWS tunneling fit in with this?
Given how big and spread out AWS is, with its services supported by computer centers all over the world, you might wonder how you can get to your specific bits and pieces without exposing them to everyone. This is where the idea of AWS tunneling comes into play. It's about making a private, secure path from your computer or network directly to your services within AWS. This way, you can reach your data, your computer programs, or your online tools as if they were right next to you, even if they are, in fact, thousands of miles away. It helps you manage your cloud setup from a distance, but with a feeling of closeness and safety, which is pretty useful, you know, when you're working across different places.
Why think about AWS tunneling?
There are several good reasons why you might want to set up an AWS tunneling connection. For one thing, it helps you keep your information private. When you connect directly to a service on AWS, especially if that service isn't meant to be seen by the general public, a secure tunnel makes sure only you, or those you give permission to, can get to it. This is really important for things like databases that hold customer details or internal tools that your team uses. It means you can work with sensitive stuff without it being out in the open, which is, in a way, a big relief for many businesses.
Keeping things secure with AWS tunneling
The core idea behind using AWS tunneling is, quite simply, to add a layer of safety. Imagine you have a locked box, and you want to move it from one room to another. You wouldn't just throw it across the room; you'd carry it carefully. In the same way, when your information travels over the internet, it's like carrying that box. An AWS tunneling setup puts your information inside another, even more secure, container for its trip. This extra layer makes it much harder for anyone who shouldn't see your information to get a peek at it. It helps keep your online work free from unwanted eyes, which is a major concern for almost everyone these days, isn't it?
What are some ways to do AWS tunneling?
There are a few common ways people set up AWS tunneling. One popular method involves using something called SSH, which stands for Secure Shell. It's a way to connect to a computer securely, and you can use it to create a kind of secure pipe for other types of network traffic. So, you might use SSH to connect to a small computer in your AWS setup, and then use that secure SSH connection to reach other services that are only visible from within your AWS cloud. It’s a bit like having a trusted guide who takes you through a private passage to get to your destination, which, in some respects, makes things much simpler and safer.
Another way to do AWS tunneling is through what's known as a Virtual Private Network, or VPN. A VPN creates a secure, encrypted link between your computer or your whole office network and your AWS cloud. It makes it seem as though your computer is actually inside the AWS network, even if you are physically far away. This is often used when you need to connect to many different services in AWS, or when you have a whole team that needs to work with your cloud setup as if they were all in the same building. It’s a pretty common way for companies to connect their offices to their cloud resources, and it works quite well for keeping things private, too.
Then there are more direct, dedicated connections, like AWS Direct Connect. This isn't exactly "tunneling" in the same software sense, but it provides a private network path from your office directly to AWS. It's like having your very own private highway to the AWS data centers, rather than sharing the public roads of the internet. This option is usually for very large businesses that need extremely fast, consistent, and secure connections for huge amounts of information. It gives you a lot of control over how your data travels, and it’s, quite honestly, a top-tier way to link up your physical location with your cloud services, offering a very stable connection.
Setting up your first AWS tunneling connection
Getting your first AWS tunneling connection going can seem like a bit of a puzzle at first, but it's really about following a few steps. If you are using SSH, for example, you would first need to make sure you have an instance, which is like a virtual computer, running in your AWS account. This instance acts as your entry point. Then, you set up your local computer to connect to that instance using SSH, telling it to forward traffic from a certain port on your machine through the secure SSH connection to a service inside AWS. There are many simple guides available that walk you through this process, and, you know, it's often much easier than it sounds once you try it out.
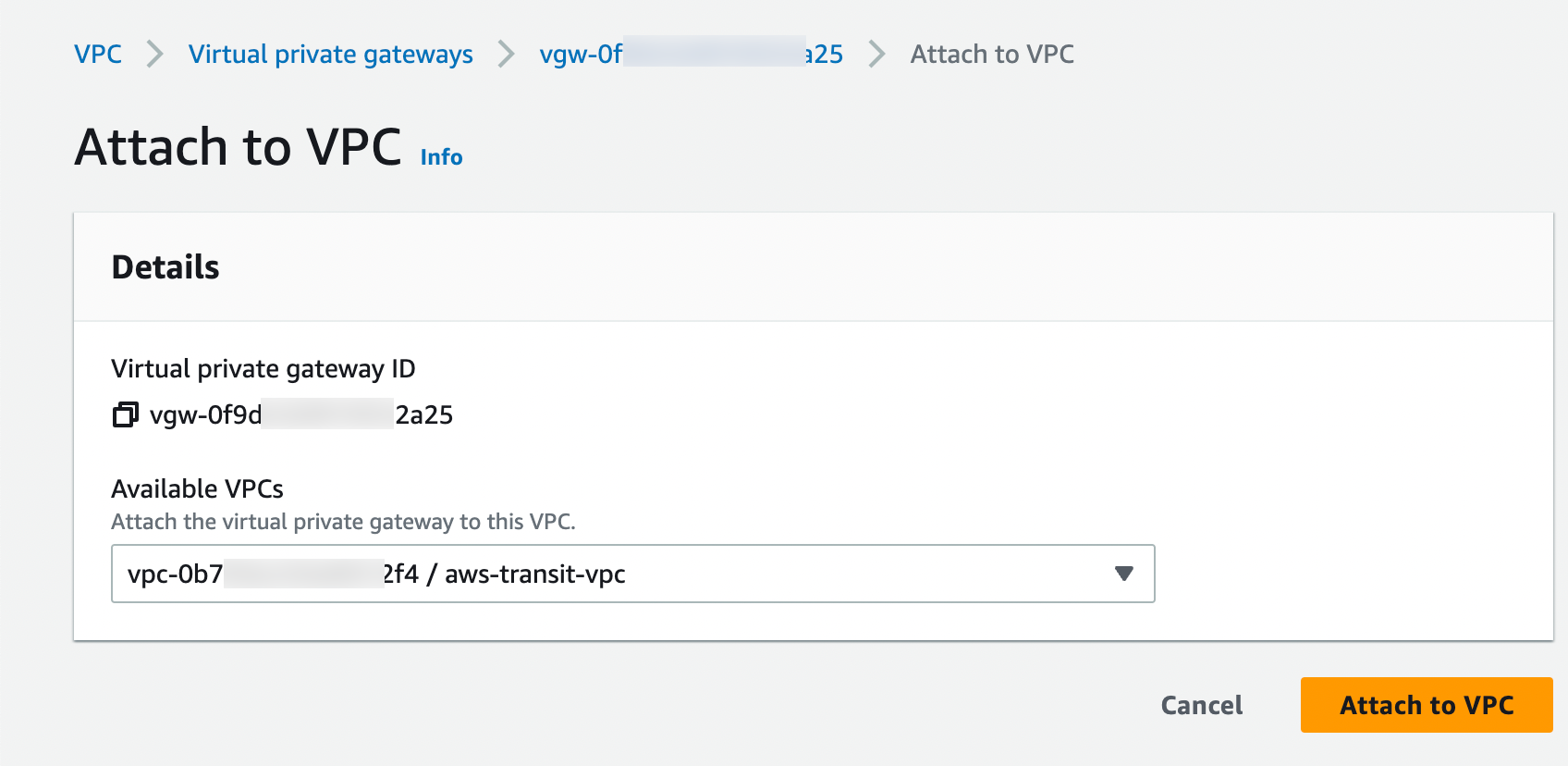
For VPNs, the setup involves a bit more network configuration, both on your side and within AWS. You create a "virtual private gateway" in AWS and then set up a "customer gateway" on your network. These two points then form the ends of your secure VPN tunnel. AWS provides tools and instructions to help you get these pieces talking to each other. It takes a little planning, but once it’s up, it usually just works in the background, keeping your connections safe. It's, in a way, like building a bridge between two separate lands so people can cross safely, and it makes accessing your AWS services feel much more seamless.
What should you keep in mind when using AWS tunneling?
When you're working with AWS tunneling, there are a few things that are good to remember. First, always make sure you are using strong ways to prove who you are, like really good passwords or special keys, for any connection you set up. This helps keep unwanted people from getting into your secure tunnels. Also, it's a good idea to only allow connections from specific places or specific people, rather than leaving your tunnel open to just anyone. This helps to make your secure path even safer, and it's a practice that, in some respects, helps keep your entire system more sound.
Another thing to keep in mind is that while AWS tunneling helps with security, it’s not the only thing you need to do. You still need to think about who can access what once they are inside your AWS setup. This means setting up proper permissions for your users and services, making sure that everyone only has access to what they truly need. It's like having a secure front door, but then also having locked doors to individual rooms inside. This layered approach to safety means your cloud environment stays protected from top to bottom, which is, basically, a very sensible way to go about things.
Finally, remember that AWS is always adding new ways to do things and making improvements. Staying up to date with their best advice and new tools can help you keep your AWS tunneling methods current and as effective as possible. There are many free services and training programs built by the folks at AWS that can help you learn more. Taking advantage of these resources means you can always be sure you are using the best ways to keep your connections safe and your cloud operations running smoothly, which is, you know, a pretty good idea for anyone using these services.
This article looked at the idea of AWS tunneling, explaining how it helps you make secure connections to your cloud resources. We talked about why it's important for keeping your information safe and explored different ways to set it up, like using SSH or VPNs. We also touched on some things to keep in mind for making sure your connections stay secure.
Related Resources:

Detail Author:
- Name : Bradford Goodwin
- Username : leannon.domenica
- Email : zula18@gmail.com
- Birthdate : 2000-03-31
- Address : 4346 King Streets Suite 576 Riceborough, IA 03350
- Phone : +1-352-600-7807
- Company : West Inc
- Job : Landscape Architect
- Bio : Est fugit aut quia et eius. Ut pariatur omnis reprehenderit praesentium. Dolores dolores magnam nulla placeat eaque omnis soluta nulla. Non sed ut optio aliquam nobis.
Socials
tiktok:
- url : https://tiktok.com/@winnifred.lehner
- username : winnifred.lehner
- bio : Aut maxime rerum cum dolorem est nam.
- followers : 3902
- following : 2232
instagram:
- url : https://instagram.com/winnifred_official
- username : winnifred_official
- bio : Occaecati aliquid illo autem veritatis. Aut fugiat doloribus eligendi quos eos.
- followers : 6337
- following : 2429
facebook:
- url : https://facebook.com/winnifred_dev
- username : winnifred_dev
- bio : Ipsam voluptatem nemo asperiores omnis aut.
- followers : 3359
- following : 2101