When we think about getting things done in the cloud, Amazon Web Services, often called AWS, really stands out. It’s like this huge, really broad place on the internet where you can find so many tools and services, over two hundred of them, all ready to go from places all over the world. This makes it a very popular choice for folks and companies looking to do things with their data and applications, so it's almost a given that many people will encounter it.
Getting started with AWS usually involves setting up your own space, a kind of digital workshop, where you can begin to build and create. The people who put AWS together want to help you get your environment ready, guiding you through the important steps so you can begin working with everything they offer. This setup process, you know, is where some important bits about how you get into your systems come into play, which is actually quite important for keeping things safe.
AWS is built to be a very adaptable and safe computing place that's out there right now. Its whole setup is made to meet the security needs of even the most sensitive groups. This focus on being secure, basically, means that how you handle your access keys, like those for SSH, becomes a really big deal for keeping your own stuff protected as well.
- Gorecenter Lcom
- Is Megan Moroney A Trump Supporter
- Sean Larkin First Wife
- Undressaicom
- Free Iot Remote Access Ssh Example
Table of Contents
- What Makes AWS a Go-To Place for Your Cloud Stuff?
- Getting Started - How Do You Set Up Your AWS Environment?
- The Core of Security - Why is AWS Built So Securely?
- Thinking About Your AWS SSH Key Management Best Practices
- What Are Some Simple Ways to Approach AWS SSH Key Management?
- Keeping Your AWS SSH Key Management Practices Tidy
- Learning More About AWS SSH Key Management
- Your Path to Better AWS SSH Key Management
What Makes AWS a Go-To Place for Your Cloud Stuff?
When you look at what makes AWS so popular, it’s really about how much it offers and how many people use it. It's like a giant online store, but for computer services, with hundreds of different options available from data centers spread across the entire globe. This widespread availability and the sheer number of services mean that almost anyone, from a small startup to a huge company, can find something that fits their needs, you know.
A big part of what AWS does is help all sorts of groups, no matter their size or what business they are in, come up with new ideas and change how they do things in fresh and exciting ways. It gives them the tools to be creative and to grow, which is pretty neat. This ability to help businesses transform is a core reason why so many turn to this particular cloud provider, and it’s a big part of its appeal, apparently.
And for those just getting their feet wet, or even for seasoned pros looking to experiment, AWS has something pretty cool: its free offerings. You can check out a good number of services, like over a hundred, without having to pay anything upfront. This makes it really accessible for people to get a feel for what’s possible, which, in a way, is a great starting point for anyone curious about cloud computing.
- Raspberry Pi Vnc Port Free
- Blake Blossom Secret
- वब एकसस आईओट डवइसस मअनग
- Lara Rose Birch ویکی پدیا
- Howie Roseman Background
Getting Started - How Do You Set Up Your AWS Environment?
Starting out with AWS means getting your own account and setting up your development area. It’s a bit like preparing a workspace before you start a big project. The platform provides clear directions to walk you through these steps, making sure your environment is all set and ready for you to begin doing your work with their services. This initial setup is quite important for a smooth start, you see.
To help you along the way, there's a whole collection of helpful papers and guides. You can find user guides that tell you how to use things, developer guides for those who build applications, references for the API, which is how programs talk to each other, and even guides for the command-line tools. These materials are there to help you figure out how to use all the different AWS products, which is really helpful, actually, for getting things right.
The Core of Security - Why is AWS Built So Securely?
One of the most striking things about AWS is how it’s put together with security in mind. It's designed to be the most adaptable and safe cloud computing place you can find today. The entire setup is built to meet the security needs of even the groups that handle the most sensitive information. This means they've really thought about keeping things locked down, which is a big comfort, in some respects.
This strong focus on security also means you can get services up and running quickly without needing to pay a lot of money right away. The underlying safety measures allow for this kind of quick action, as the platform itself handles many of the general security concerns. This approach, you know, lets users focus more on their projects and less on building a secure foundation from scratch, which is pretty convenient.
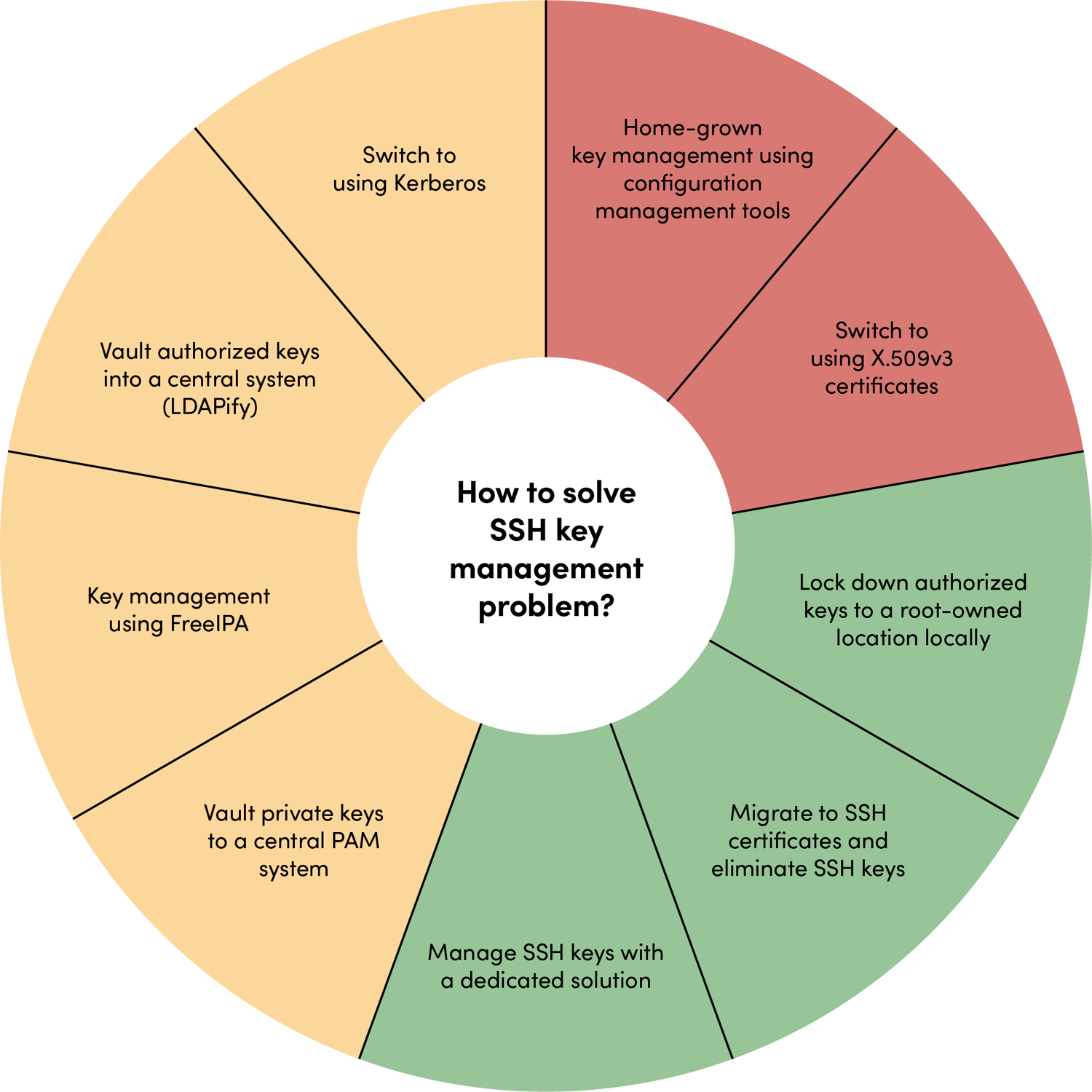
Thinking About Your AWS SSH Key Management Best Practices
Given how secure AWS itself is, it makes sense that how you manage your own access tools, like SSH keys, needs to be just as careful. If the house is built with strong walls and good locks, you still need to make sure your own key to the front door is kept safe. This thought process is a big part of what makes up good aws ssh key management best practices, helping you keep your part of the cloud safe and sound.
AWS offers a wide range of cloud service options as your provider, covering things like computing power, places to store your information, databases, ways to connect networks, data lakes for big data, and even tools for machine learning and artificial intelligence. For each of these services, your SSH keys might be a way you get in and work with them. So, thinking about how you handle those keys across all these different areas becomes very important for your aws ssh key management best practices.
What Are Some Simple Ways to Approach AWS SSH Key Management?
When it comes to your SSH keys, it’s helpful to think of them like the keys to your home or your car. You wouldn't just leave those lying around for anyone to pick up, would you? The same idea applies to your digital keys that let you get into your AWS systems. Keeping them in a secure spot and making sure only the right people have access is a pretty basic but extremely important step for your aws ssh key management.
Even though AWS has a very strong security setup, a lot of the day-to-day safety of your own operations still depends on the actions you take. It's like having a really secure bank vault; the bank does its part, but you still need to be careful with your debit card and PIN. Your carefulness with your SSH keys is a direct part of keeping your cloud environment secure, which, in a way, is a personal responsibility.
Keeping Your AWS SSH Key Management Practices Tidy
One good habit for your aws ssh key management is to regularly check who has access and which keys are out there. It’s a bit like doing a spring cleaning of your digital access points. If someone no longer needs access, or if a key hasn't been used in a while, it might be time to remove or update it. This helps keep things neat and reduces the chances of unwanted access, you know.
Another helpful step is to change your keys from time to time. Think of it like changing the locks on your house every so often, just to be extra safe. Even if a key hasn't been compromised, refreshing it can add an extra layer of protection. This practice, sometimes called key rotation, is a simple but effective part of strong aws ssh key management best practices, making it harder for old or forgotten keys to be a problem.
Learning More About AWS SSH Key Management
To really get a good handle on your aws ssh key management, it's a good idea to go back to those product guides and references. They're full of helpful information, from user guides that show you how to do things step-by-step to developer guides that explain the technical bits. These resources are put together to help you understand the different ways you can work with AWS products, which is quite useful, honestly.
Looking through the API references and command-line interface references can also give you a deeper insight into how the systems work and how you can manage your keys programmatically. These documents are like blueprints for interacting with AWS services, and they often contain subtle hints about secure ways to handle access. So, taking the time to explore these materials can really help you refine your aws ssh key management best practices, giving you a better handle on things.
Your Path to Better AWS SSH Key Management
AWS gives you the tools and the secure environment, but how you use those tools, especially when it comes to your SSH keys, makes all the difference. It's like having a very well-built workshop; the tools are there, but your skill and care in using them determine the quality of what you create. Your careful approach to aws ssh key management is your part in keeping your digital space secure, you see.
Ultimately, a good approach to key management supports the bigger picture of what AWS helps organizations do: innovate and change their business in new and exciting ways. When your access is secure and well-managed, you can focus on building and creating without constantly worrying about unauthorized access. This peace of mind, basically, lets you use the cloud to its fullest potential, which is pretty cool.
This article has covered how AWS is a broad and widely used cloud platform, its secure architecture, how to get started with setting up your environment, and the importance of good SSH key management practices. It touched on how documentation helps, why security is built into AWS, and how your own key handling contributes to overall safety.
Related Resources:


Detail Author:
- Name : Randi Bashirian
- Username : tbarton
- Email : eva16@yahoo.com
- Birthdate : 1988-09-20
- Address : 147 Furman Station North Malindamouth, SD 47465-3063
- Phone : 630-873-1511
- Company : Barton Inc
- Job : Manager of Food Preparation
- Bio : Maiores tenetur sit consectetur occaecati molestias dicta. Quia sint ipsa qui et voluptatem deserunt nemo iste. Et esse natus nam quos praesentium enim ab recusandae.
Socials
instagram:
- url : https://instagram.com/ruecker1979
- username : ruecker1979
- bio : Ullam omnis quas ut quo. Qui inventore id pariatur id soluta quia.
- followers : 3708
- following : 1613
linkedin:
- url : https://linkedin.com/in/rruecker
- username : rruecker
- bio : Velit et quo ut facere ea.
- followers : 226
- following : 1738
facebook:
- url : https://facebook.com/ruecker1990
- username : ruecker1990
- bio : Blanditiis voluptate et voluptate asperiores quia sit.
- followers : 4355
- following : 2747
tiktok:
- url : https://tiktok.com/@rueckerr
- username : rueckerr
- bio : Enim aut voluptatum provident quis.
- followers : 3068
- following : 835